Attach artifacts
In this example, we will attach SBOMs to images. The workflow is similar for attaching signatures/attestations to an artifact.
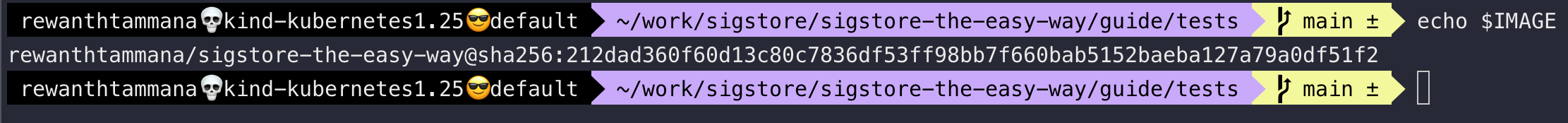
Set image
We can follow the steps from this section to set the image. Let's ensure the IMAGE variable is set.
echo $IMAGE
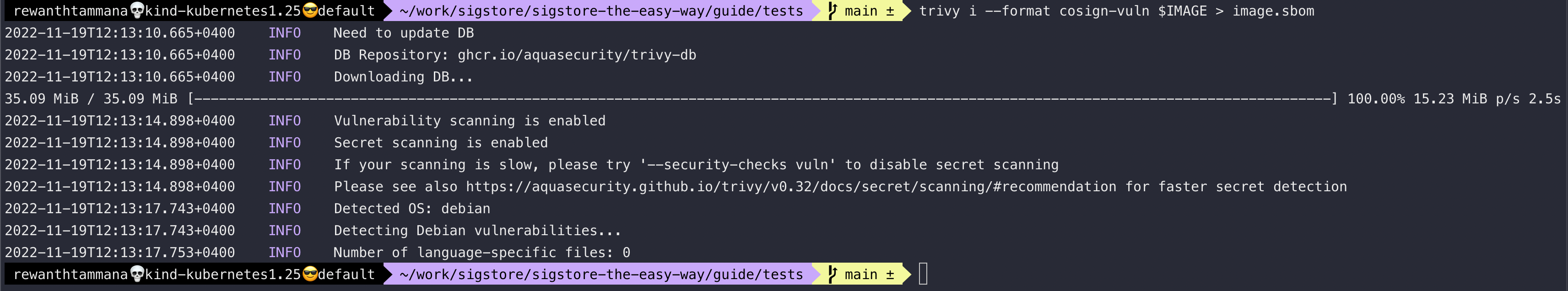
Generate SBOM for the image
The SBOM contains the list of dependencies & vulnerabilities in it (depending on how its generated). SBOM section decrypts the below command & its output in great detail. It explains more about SBOMs as well.
trivy i --format cosign-vuln $IMAGE > image.sbom
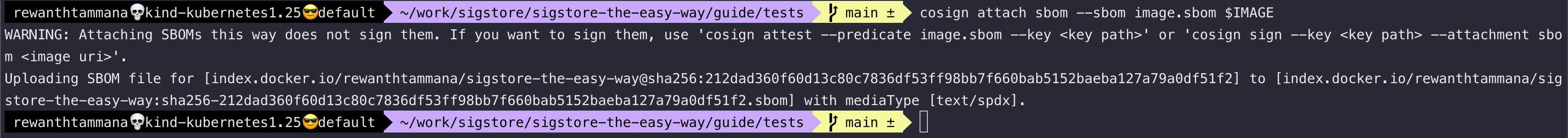
Attach SBOM with the image
It's recommended to keep track of all the known vulnerabilities when committing/pushing an image. We will attach the above-generated SBOM to the image & push it to the registry.
cosign attach sbom --sbom image.sbom $IMAGE
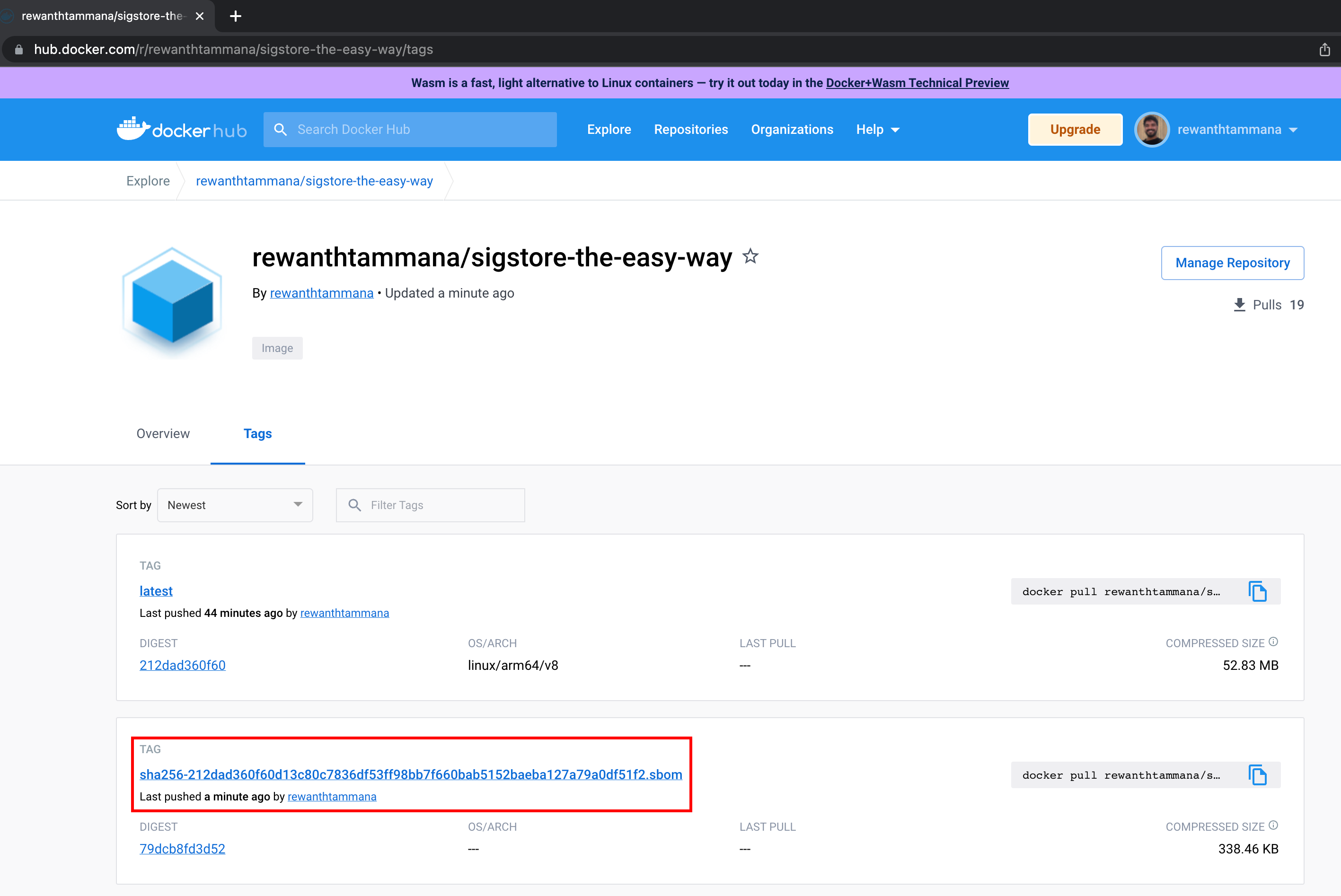
We can see the SBOM artifact uploaded to the registry. In this case, it's dockerhub.
NOTE
The attach feature only uploads the provided artifact to the registry. It doesn't sign the artifact, so anyone can tamper with it & there's no way to verification. To sign artifacts like SBOMs, etc., we have to attest the artifact instead of attaching it.
Created: 2022-11-19 06:59:59