Generate SBOM
Multiple tools help us to generate SBOMs for docker images, OCI artifacts, SIF images, filesystems, etc.
Docker
We will use docker to generate the SBOM.
docker sbom $IMAGE > image.sbom
Docker CLI uses syft in the background. For extensive usage & customizations, we can download syft.
Syft
We will use syft to generate the SBOM.
syft packages $IMAGE > image.sbom
Trivy
We will use trivy to generate the SBOM.
The cosign-vuln format is a custom type created by trivy to store SBOM data along with the list of vulnerabilities & associated CVEs. This is really helpful to review the list of vulnerabilities at the time of packaging & now.
trivy i --format cosign-vuln $IMAGE > image.sbom
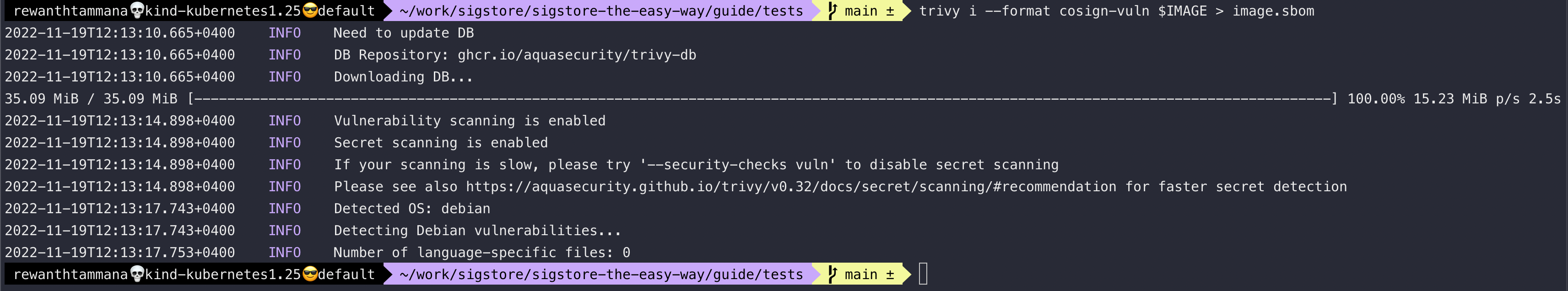
We can query the above-generated SBOM to extract information like a list of CVEs, dependencies, etc.
cat image.sbom | jq -r '.scanner.result.Results[].Vulnerabilities[].VulnerabilityID' | wc -l
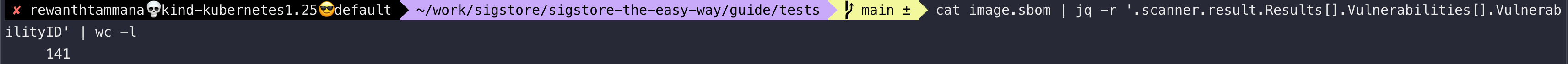
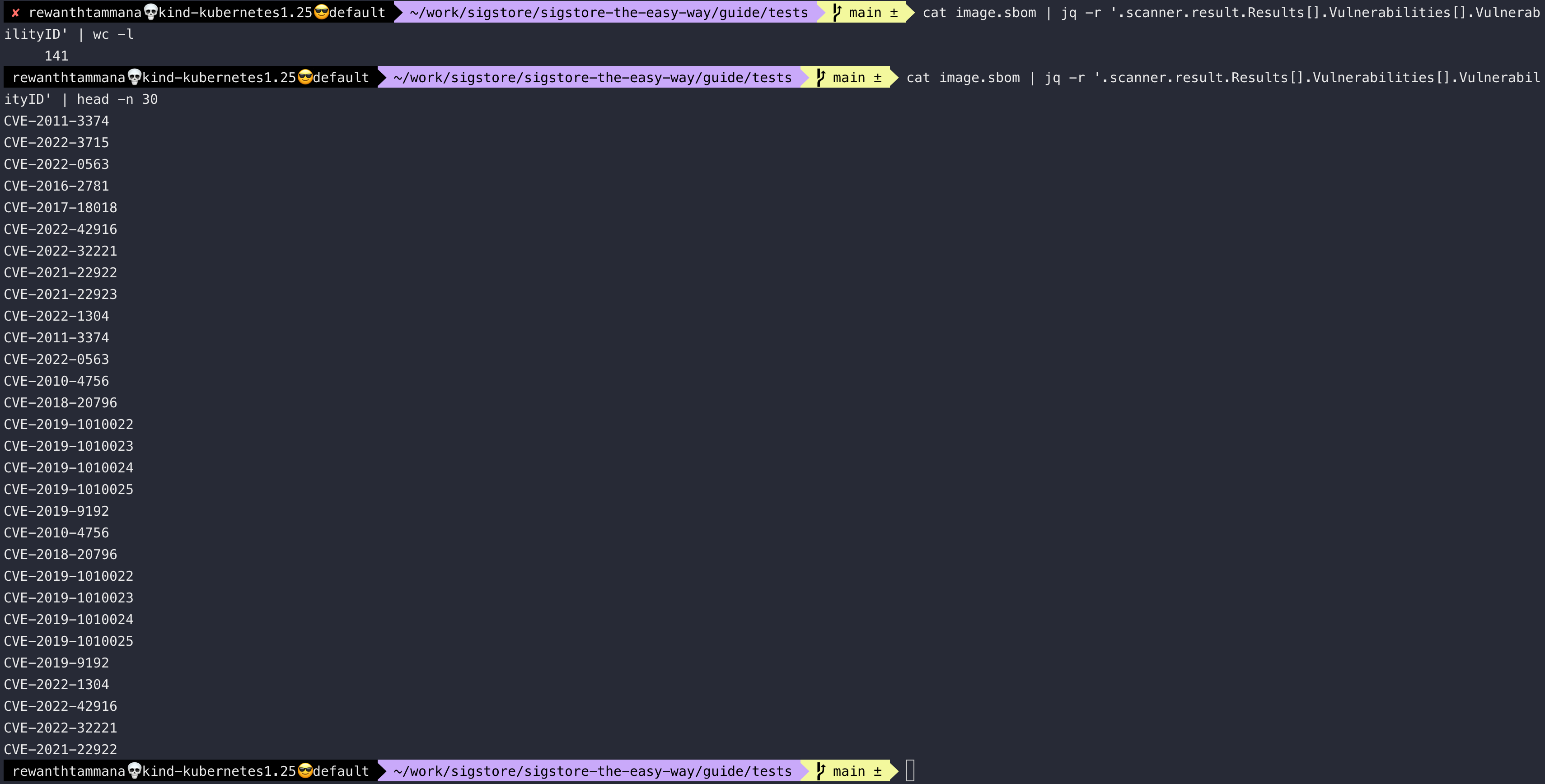
As you can see above, there are 141 CVEs in your image (i.e., nginx image as we re-tagged it). Let's list the first 30 CVEs from the list.
cat image.sbom | jq -r '.scanner.result.Results[].Vulnerabilities[].VulnerabilityID' | head -n 30
Created: 2022-11-19 06:59:59