Attest and verify artifacts
In this example, we will attest SBOMs. The workflow is similar for attesting signatures/attestations.
Set image
We can follow the steps from this section to set the image. Let's ensure the IMAGE variable is set.
echo $IMAGE
Generate SBOM for the image
SBOM section decrypts the below command & its output in great detail. It explains more about SBOMs as well.
trivy i --format cosign-vuln $IMAGE > image.sbom
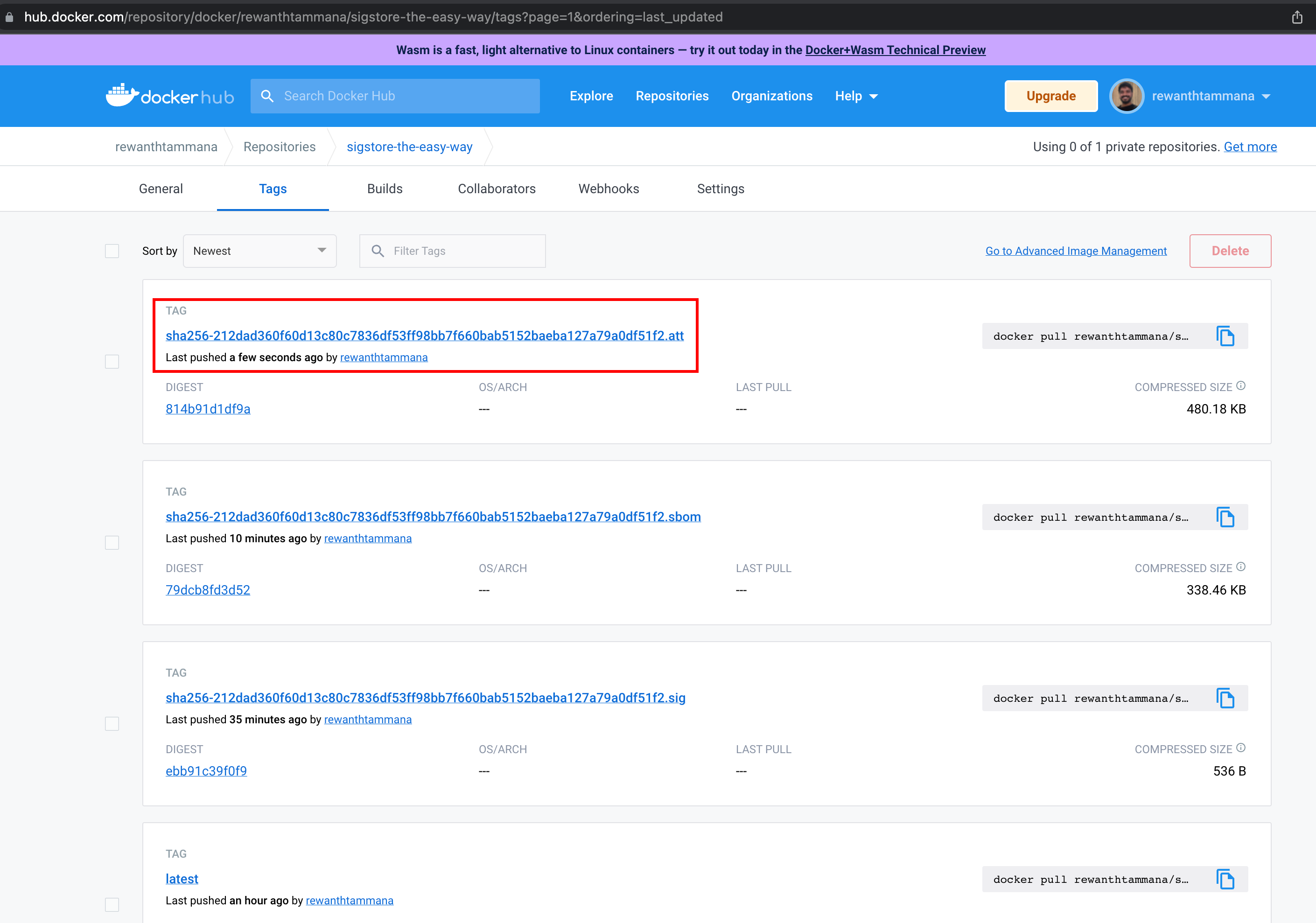
Attest and push the sbom to OCI registry
We will attest the generated image.sbom as the source of truth, sign it with the private key & push it to the registry.
cosign attest --key cosign.key --predicate image.sbom $IMAGE

We can see the attested artifact uploaded to the registry. In this case, it's dockerhub.
Verify the sbom of the image from registry
In the future, whenever we want to validate the SBOM of the image, we can verify it with the below command.
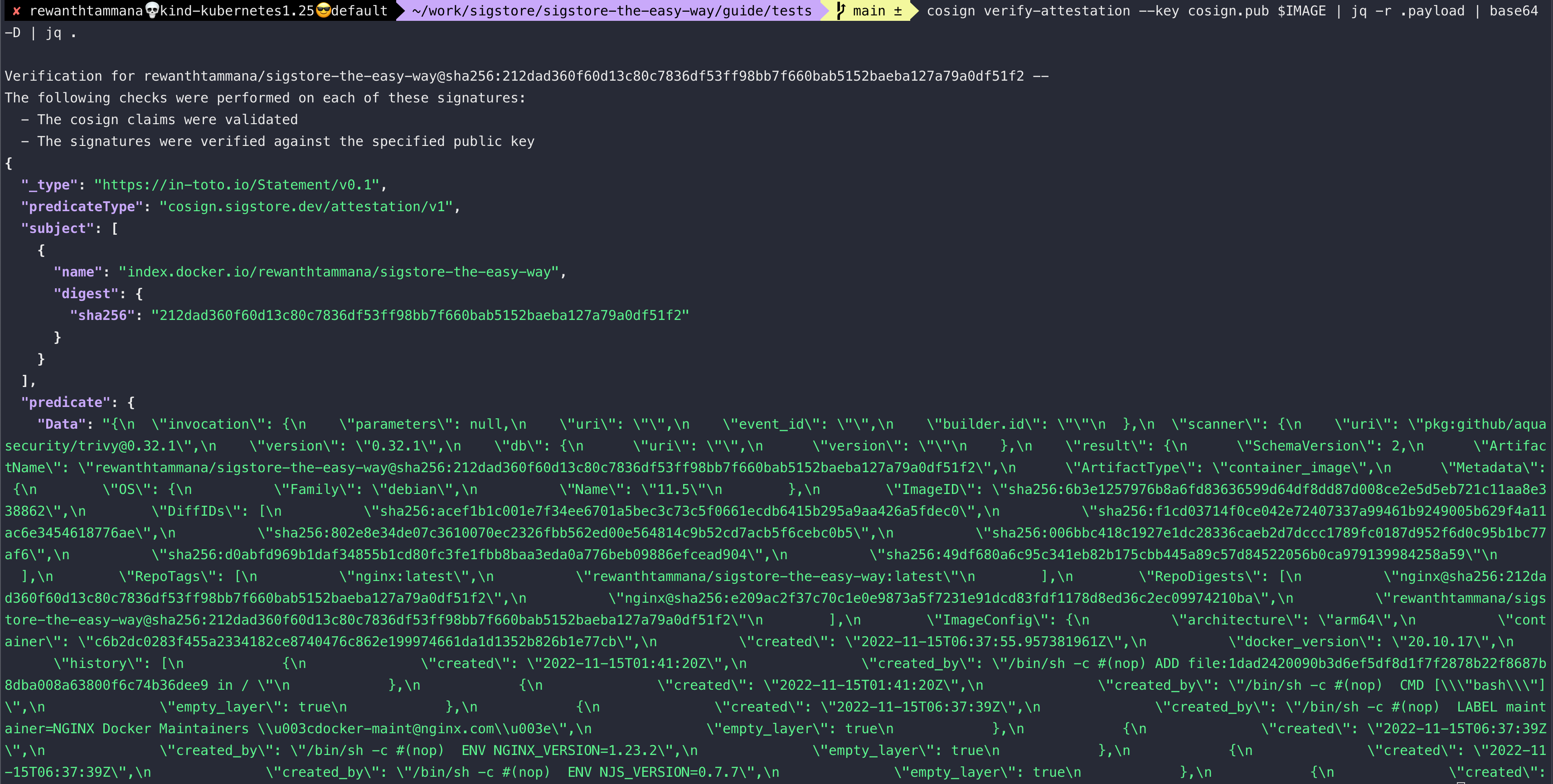
cosign verify-attestation --key cosign.pub $IMAGE
Extract artifact from the registry
The above command verifies & returns the uploaded artifact data in base64 format. We can decode it to query the artifact (in this case, the SBOM file).
cosign verify-attestation --key cosign.pub $IMAGE | jq -r .payload | base64 -d | jq .
Created: 2022-11-19 06:59:59